Digital information exchange is paramount, and the security of sensitive data is equally as significant. Various encryption algorithms must be deployed to maintain the highest levels of security, ensuring the integrity and confidentiality of digital communication channels. One such essential technique is Transport Layer Security (TLS). This comprehensive discussion aims to delve into the intricate details of TLS, analyze its potential vulnerabilities, and strategize its effective utilization.
What is TLS: Understanding the Transport Layer Security (TLS) Protocol
Transport Layer Security (TLS) is a standard protocol that facilitates authentication, privacy, and data integrity in interactions between two computer applications. TLS is the most extensively used security protocol today, ideal for applications that require secure data transfer over a network, including web browsers, file transfers, VPN connections, remote desktop sessions, and VoIP. TLS is also being incorporated into modern cellular transport technologies like 5G to safeguard core network functionalities across the radio access network (RAN).
At its core, TLS is a cryptographic protocol that provides communications security over computer networks. Widely used for internet communications and online transactions, TLS aims to ensure privacy and data security between communicating applications and their users over a web server. However, it’s critical to remember that while TLS secures the communication channel, it does not inherently encrypt the payload, leaving it in plaintext and potentially exposing it to security vulnerabilities under certain conditions.
“Good Enough” Isn’t Always Good Enough
Ensure your sensitive data is delivered securely, regardless of the recipient’s endpoint. Learn more about our advanced encryption standard and secure exchange integrations today.
TLS vs. Secure Sockets Layer (SSL)
When discussing encryption algorithms, TLS and SSL protocols are often used interchangeably, but it’s important to understand the minute distinctions to make informed decisions regarding data security and compliance. TLS is the more modern and secure protocol. It protects data while being transferred between applications over a web server. In contrast, SSL, TLS’ predecessor, was commonly used to secure web server communication channels before the adoption of email encryption. Today, both play a crucial role in securing different parts of the email process.
When an email is sent, either TLS or SSL protocols can encrypt the connection from the sender’s mail server to the recipient, preventing unauthorized access and interception of the email content during transmission. It’s important to understand that both TLS and SSL protocols do not encrypt the actual email content, only the connection. To achieve end-to-end encryption, additional data protection measures are necessary, such as using a specialized secure data exchange solution, like DataMotion’s secure message center, to ensure the secure handling of sensitive information.
Opportunistic TLS: A Beneficial Yet Risky Solution
The spotlight is often cast on Opportunistic TLS, an automatic variant of TLS that aims to secure data transmission. Its allure lies in its ability to establish a secure TLS connection without requiring user intervention. This balance between usability and security is appealing but has its shortcomings. The trade-off of this intuitive approach is often the inadvertent transmission of sensitive data over public networks without encryption. Consequently, reliance on Opportunistic TLS risks non-compliance with stringent data protection regulations.
Investigating Breach Scenarios in Opportunistic TLS
The potential for security vulnerabilities of Opportunistic TLS is particularly noticeable in two common scenarios. In the first instance, when the recipient’s email system does not support TLS, Opportunistic TLS fails to establish an encrypted connection. The system falls back to unencrypted transmission, exposing security vulnerabilities and sensitive data to threats.
For instance, many major cloud email providers like Gmail and Yahoo Mail have been using TLS to secure their email connections for several years. In Gmail, you’ll recognize that a message was sent over TLS by clicking on the ‘details’ of the message. If you see “Standard (TLS)” on web or the lock icon in the Gmail app on your mobile device, you’ll know that your message was sent securely. However, for TLS to work, the receiving server must also employ TLS encryption. If your recipient does not, then Gmail will revert to unencrypted transmission, leaving your message content vulnerable to a breach.
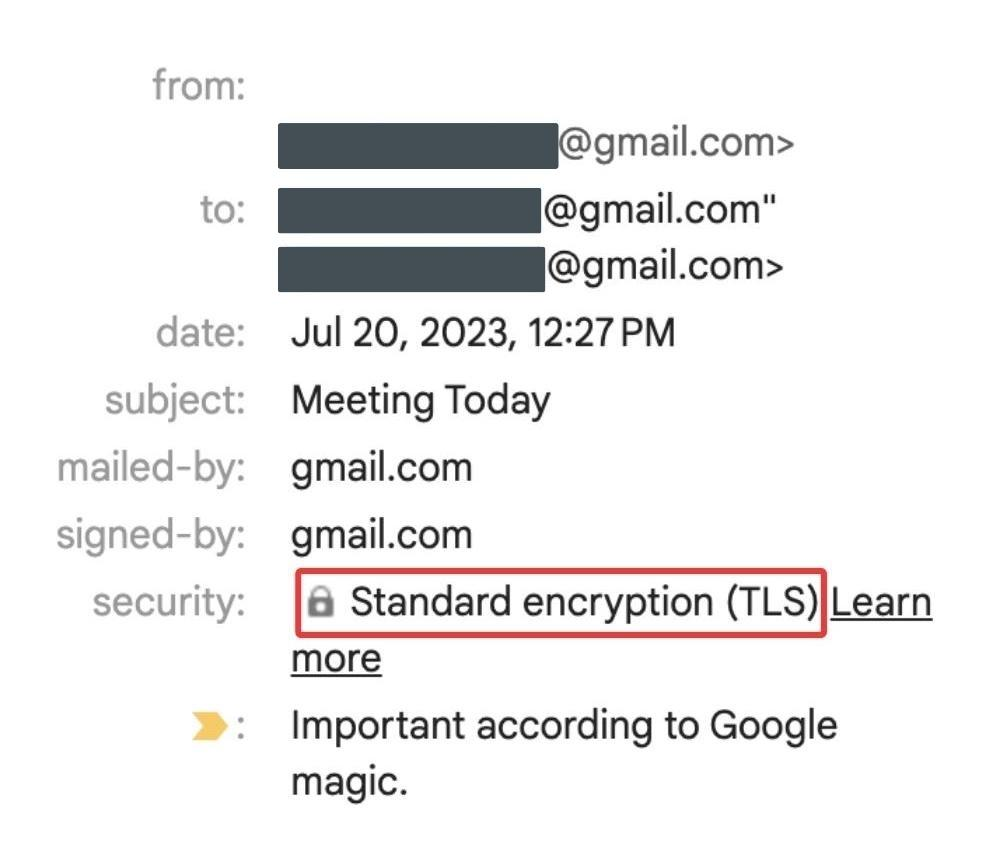
The second scenario arises when the recipient uses a cloud-based anti-virus or anti-spam service. Despite supporting TLS for receiving emails, these services often create a false sense of security. The sender system may be under the illusion that the message has been delivered securely, while in reality it was delivered securely to the intermediary (the anti-virus or anti-spam service). However, the journey from this intermediary to the recipient’s email server often lacks TLS encryption, leading to an unencrypted transmission over public networks and a breach in compliance.
Demystifying Misconceptions Surrounding TLS and SPAM/Anti-Virus Services
Further exploration into email encryption algorithms necessitates debunking misconceptions about TLS and SPAM/Anti-Virus services. While it’s true that these services contribute to data protection, they do not guarantee comprehensive security. A decisive factor in securing data is ensuring the secure transfer of messages via a TLS-enabled connection. Potential security vulnerabilities can emerge when this level of protection is absent, opening the door to possible data breaches.
Moreover, assuming that all replies to messages received over a TLS connection are inherently secure is erroneous. The validity of this assumption hinges on whether the recipient’s web server employs TLS encryption for outgoing messages, which is contingent on the recipient’s IT policy.
Defining Robust Compliance Strategies
In the quest for data security, organizations must recognize the importance of implementing secondary protective measures alongside TLS. Mechanisms like two-factor authentication, secure portal logins with unique recipient passwords, or setting a lifespan for messages offer additional layers of protection. These protocols enhance data security and mitigate the risk of breaches, even when potential security vulnerabilities exist in the recipient’s primary email account.
Maximizing the Benefits of Secure Data Delivery Systems
Advanced secure data delivery systems like DataMotion’s secure message center offer an integrated solution to address concerns around data security. By supporting various delivery methods, including clickless SafeTLS, these platforms facilitate the safe exchange of sensitive information across a wide range of recipients while ensuring adherence to privacy regulations. Instead of falling back to unencrypted delivery, the secure message center provides end-to-end encryption for messages that cannot be sent with TLS. Additionally, by offering simple methods for recipients to securely reply to the sender, it reduces the risk of sensitive data being exchanged over an insecure communication channel. Implementing such systems underlines the importance of ensuring end-to-end encryption between email systems before enabling TLS.
Concluding Thoughts: Leveraging TLS and Beyond for Enhanced Data Security
Navigating the digital landscape, it becomes clear that while TLS is a powerful tool, there are more encompassing solutions for resolving security vulnerabilities. Its effectiveness depends largely on correct implementation, integration with existing workflows, and additional security measures in place. Organizations handling sensitive data must approach reliance on TLS or Opportunistic TLS cautiously. Implementing a comprehensive data delivery system that ensures end-to-end security can provide a challenging line of defense, ensuring that digital communication channels remain confidential and secure. As we continue to work to understand the continually evolving domain of data security, gaining proficiency in encryption algorithms like TLS and formulating robust data security strategies is critical.
Don’t compromise on your data security. Learn more about DataMotion’s comprehensive secure data exchange solutions, like our secure message center and our robust integrations, by contacting our sales team today. Subscribe to the DataMotion Newsletter to stay informed on the latest advancements in data security, industry best practices, and other thought leadership.




