Sensitive business data is more vulnerable today than ever before. Corporate trade secrets, national security information, personal medical records, Social Security and credit card numbers are all stored, used, and transmitted online and through connected devices. The proliferation of valuable data provides cybercriminals with an increasingly wide range of opportunities to monetize stolen information and intellectual property. In addition, foreign governments and organized crime rings have embraced hacking as one of their most potent tools. Organizations are also at risk from insider threats and social engineering attacks. A negligent or disgruntled employee can expose confidential information even faster than a hacker if there aren’t adequate safeguards in place to prevent the accidental or intentional release of sensitive data.
Data privacy is critical, but it can’t come at the expense of your ability to complete daily tasks. DataMotion has led the information security industry for over two decades, providing cutting-edge data and email security. Through flexible APIs and seamless integrations, including support for platforms like Microsoft Cloud and Salesforce, we offer secure digital exchange and AI-powered communications that enable compliance and operational efficiency across industries. In this article, we’ll examine best practices around securing data at rest, in use, and in motion as well as how to conduct a holistic data security risk assessment. We will also show you how DataMotion’s secure messaging and document exchange solutions keep your data platforms safe.
The Three Critical Components of a Total Information Security Strategy
Techniques to secure data must address all three states: data at rest, in use, and in motion. Common security measures include:
- Encryption (e.g., AES-256 for data at rest, TLS for data in motion)
- Access controls based on least privilege and role-based permissions
- Multi-Factor Authentication (MFA) to verify user identity
- Data Loss Prevention (DLP) to monitor and block data leaks
- Regular backups and disaster recovery planning
- Network segmentation to isolate critical infrastructure
- Continuous monitoring for real-time threat detection
These layered protections form a comprehensive data security strategy that defends against both external breaches and insider threats.
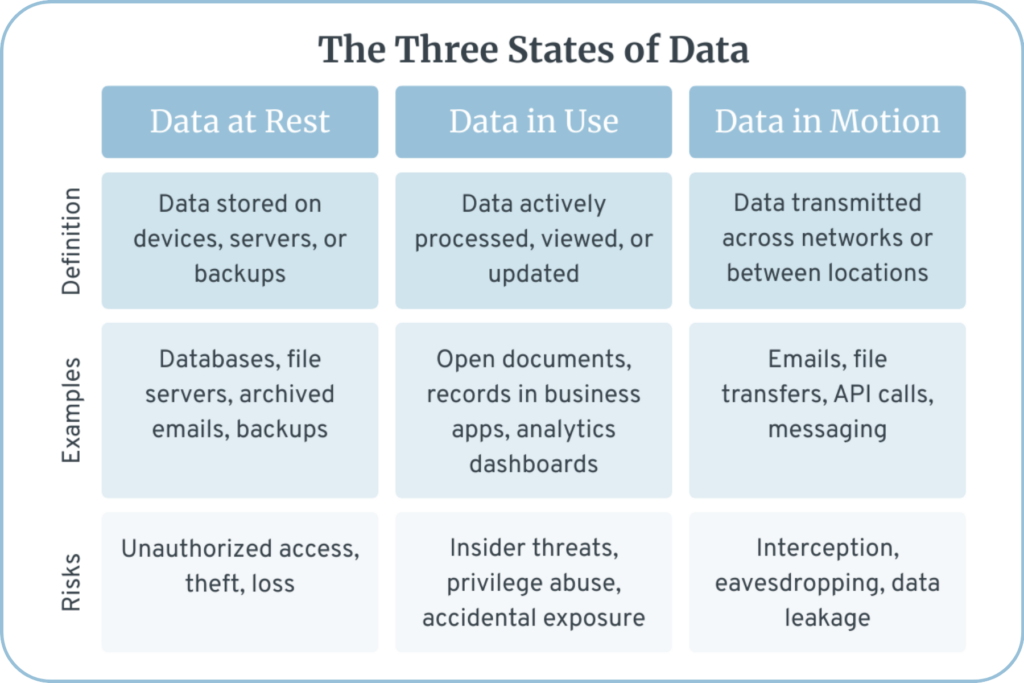
Data at Rest
Data is considered to be “at rest” when it is stored on a non-volatile storage medium, such as a hard drive, solid-state drive, or in cloud storage. In this relatively secure state, sensitive information such as Personal Identifiable Information (PII), Personal Health Information (PHI), and otherwise confidential enterprise data is primarily protected by conventional, perimeter-based defenses such as firewalls and anti-virus programs. However, these barriers are not impenetrable, and a data breach is still possible. Organizations need additional security measures to protect sensitive data from intruders in the event that the network is compromised.
Encrypting hard drives is one of the best, most effective security measures to ensure the safety of your enterprise’s data at rest. In the event of a data breach, your data will be rendered unreadable to cybercriminals, making it worthless. There are other steps you can take that also help, such as implementing access controls and storing individual data elements in separate locations. This extra step greatly decreases the likelihood of attackers gaining enough information to commit fraud or other crimes. One way in which DataMotion mitigates the risk of data leakage is through our zero-trust security approach, which goes beyond perimeter protection, offering high-level data security from the inside out.
Data in Use
We just spoke to the importance of securing sensitive data when it is at rest, often through data security measures like encryption. However, data in use is especially vulnerable to theft, and therefore requires additional security protocols. This is because, by the “in use” definition, the data must be accessible to those who need it. The greater the number of people and devices that have access to the data, the greater the risk that it will end up in the wrong hands.
There are two major keys to securing data while in use. The first is to control access as tightly as possible. Not everyone in your enterprise will need access to every piece of data, and there should be data privacy permissions and protocols in place. Data Loss Prevention (DLP) solutions can also help enforce policies on how data in use can be handled. The second key is to incorporate some type of authentication to ensure that users are who they say they are and aren’t hiding behind stolen identities. While multi-factor authentication (MFA) is now standard practice, leading organizations are adopting continuous authentication and adaptive access controls to detect risks throughout a session – not just at login.
Organizations also need to be able to easily track and report relevant information so they can detect suspicious activity, diagnose potential threats, and proactively improve security. For example, an account being disabled due to a certain number of failed login attempts could be a warning sign that a system is under attack.
Data in Motion
Data is at its most vulnerable to data leakage when it is in motion and securing information in this state requires specialized encryption standards and strong security. This includes not only email, but also data transferred via secure file transfer protocols, APIs, cloud-to-cloud communication, and internal network traffic. Our expectation of immediacy dictates that a growing volume of sensitive data be transmitted digitally—forcing many organizations to replace couriers, faxes, and conventional mail service with faster options such as email. With over 347 billion emails sent and received every day, email remains a primary target for cyberattacks – particularly as threats like AI-powered phishing and business email compromise attacks continue to increase.1
When you send an email, it typically takes a long and winding journey through the digital infrastructure at enterprises, healthcare organizations, universities, government facilities, and other network locations. Anyone with the right tools can intercept your email as it moves along this path, which is where the need for increased email security and secure email gateways comes in.
There are a number of effective ways to secure data in motion. The best method to ensure that your messages and attachments remain confidential is to transmit them through an easy-to-use data encryption platform that integrates with your existing systems and workflows. This not only prevents careless mistakes, but ease of use helps mitigate risky shortcuts. Users should be able to send and receive encrypted messages directly from their standard email service. More than 29% of organizations place this capability on their email encryption and customer experience ‘wish list’.2
Email remains one of the biggest threats to data security in most organizations. Sending sensitive data and documents without proper encryption introduces serious risk, especially as the threat landscape continues to evolve. Email is vulnerable to a number of cyberattacks, including phishing, spoofing, spam, and now more sophisticated AI-generated social engineering attacks that can mimic human behavior with alarming precision. It’s easy for hackers to intercept sensitive data as it travels from Point A to Point B. Encrypting data while in motion is a critical first line of data privacy, as high encryption standards will render stolen data unreadable. For large files or highly sensitive exchanges, secure file transfer protocols or managed file transfer (MFT) solutions offer enhanced security and tracking. But encryption alone is not enough. Enterprises must layer in policy-based security protections like secure email gateways, multi-factor authentication, employee security training, and real-time anomaly detection. With AI now amplifying threat complexity, continuous monitoring and adaptive defenses are essential.
The encryption service your organization uses should be used for desktops and all user devices with data access. It is also important that the service offers and supports mobile email applications. With most email opens now occurring on mobile devices, secure mobile access is non-negotiable, especially with the widespread use of encrypted messaging apps, hybrid SaaS, and eSIM-based device authentication. Yet, 39% of organizations say users still face limited options for securely interacting across devices.2
Want to dive deeper?
Download The Definitive Guide to Data Exchange: Managing Structured & Unstructured Data to explore how secure, intelligent workflows can transform your data strategy.
How to Conduct an Effective Risk Assessment
Unless your organization has recently conducted a data security risk assessment, the threat of a data breach is probably much larger and more immediate than you realize. Organizations often underestimate their risk because they believe all their sensitive data is contained within a few secure systems. They feel access to this sensitive data is restricted to only those who need it. This is rarely true.
To understand the full scope of potential data exposure, it helps to examine security through the lens of day-to-day workflows. With remote and hybrid work now standard, employees regularly access sensitive information from personal, mobile, and cloud-connected devices. That flexibility, while necessary, increases your attack surface – especially when data flows across apps, networks, and jurisdictions with varying security and compliance requirements.
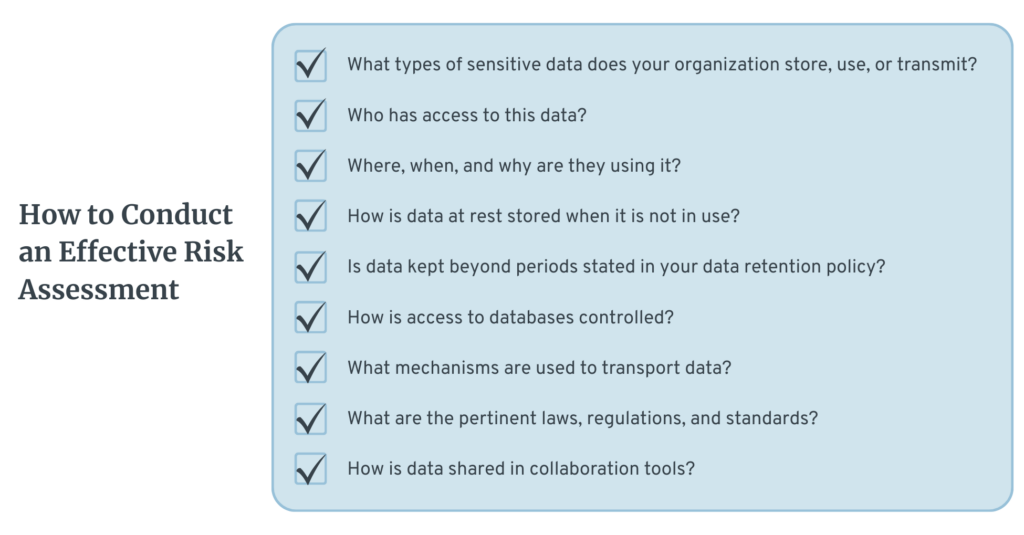
Inevitably, information is going to end up spread across multiple devices and networks with varying degrees of security and risk. Before you can take effective action to mitigate your risk you need to identify where your risks of a data breach lie. You should conduct a thorough security risk assessment, starting with a data privacy and email security review. Such a review will identify vulnerabilities within your organization and where they lie. This assessment should provide answers to core questions, including:
- What types of sensitive data does your organization store, use, or transmit?
- Who has access to this data?
- Where, when, and why are they using it?
- How is data at rest stored when it is not in use?
- Is data kept beyond periods stated in your data retention policy?
- How is access to databases controlled?
- What mechanisms are used to transport data?
- What are the pertinent laws, regulations, and standards?
- How is data shared in collaboration tools?
Once you have a solid grasp of the potential risks, we recommend that you work with data security experts to determine the steps needed to implement a total information security strategy. This strategy will likely include aspects such as a data retention policy, data sharing policy, an incident response plan, and implementing a policy based on the principle of least privilege.
Data vulnerability assessments should be truly holistic and not just look for threats within your organization for an effective risk management strategy. If your vendors have vulnerabilities, then your enterprise does as well. We recommend checking in regularly with your vendors about current and planned security protocols and exploring a vendor consolidation strategy. When checking in or vetting a single vendor as part of a consolidation strategy be sure to ask the right questions about security protocols.
Furthermore, an effective risk management strategy involves continuous monitoring and regular assessments, not just a one-time review, to adapt to new threats and changes in your data environment.
Don’t wait for the risks to your data and email security to make themselves known; by that time, it will be too late to take any effective action.
Summary
Your enterprise data is incredibly valuable to both your organization and cybercriminals. Data security measures should be high on your business process priority list. Leaving security to chance puts you at risk of joining the long and growing list of organizations that have learned painful first-hand lessons about data security, including Target, Home Depot, Anthem, the Federal Office of Personnel Management, and the National Security Agency.
DataMotion’s platform protects data at rest, in use, and in motion by offering ironclad security that includes military-grade encryption standards, a governed database, a zero-trust security approach, and data tracking and monitoring. Visit our website to learn more about how we can help your enterprise’s data and email security measures or contact our team of security experts today for an introductory call.

1. The Radicati Group. “Email Statistics Report, 2023–2027.”
2. DataMotion. “Compliance Issues Plague Customer Engagement: Customer Engagement Trends in Financial Services and Insurance.”


