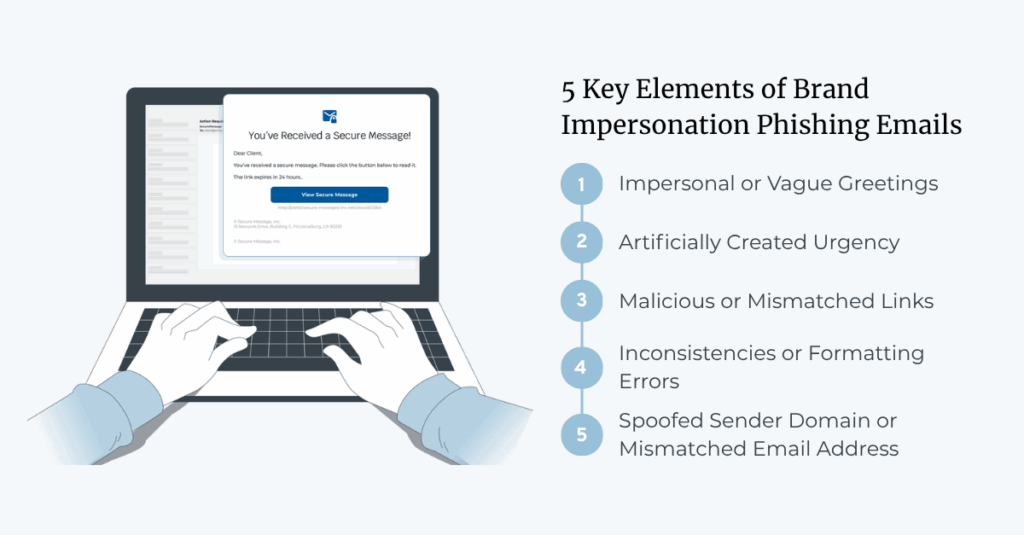
Not all ‘secure’ communication tools are what they seem. In fact, some of the same portals and branded notifications meant to protect your data have become prime targets for brand impersonation phishing and credential harvesting. For regulated industries, that risk is a daily exposure point hiding behind “secure” workflows your users already trust.
Let’s look at why, and what regulated enterprises can do to close this growing security gap.
The False Promise of “Secure” Tools
Third-party “secure” email and file-sharing tools promised safety and convenience. In practice, they’ve created two persistent challenges for regulated enterprises:
- Friction: Extra logins, unfamiliar portals, and confusing handoffs disrupt user experience.
- A Growing Phishing Attack Surface: Attackers now impersonate “secure message” notifications and file-share links, turning trusted workflows into brand impersonation phishing traps.
This isn’t hypothetical. Threat actors are actively abusing trusted cloud platforms, file-sharing tools, and “secure message” workflows to harvest credentials and bypass defenses. Microsoft, for example, has documented campaigns that misuse legitimate file-hosting services like SharePoint, OneDrive, and Dropbox to evade detection and phish identities.
Why Attackers Love Third-Party “Secure” Workflows
When users see a familiar logo or a “You have a secure message” alert, their guard naturally drops. Attackers know this, and multiple security vendors have reported real-world phishing campaigns that abuse this trust:
- Dropbox-Themed Phishing: Observed in the wild, these attacks use adversary-in-the-middle (AiTM) techniques and legitimate-looking Dropbox notifications that route to credential traps.
- Zix Impersonation: Spoofed “Secure Zix message” emails that mimic encrypted-mail workflows to steal login credentials.
Zooming out, the macro data reinforces the risk narrative. The FBI’s 2024 Internet Crime Report ranks phishing and spoofing as the top complaint category, with cybercrime losses reaching a record $16.6B—a 33% increase year-over-year. While Verizon’s 2025 Data Breach Investigation Report confirms that phishing and pretexting remain among the leading social-engineering tactics behind costly breaches.
The pattern is clear: the more “secure” tools rely on external portals and branded notifications, the more attackers can exploit user trust.
The Architectural Fix: Bring Secure Interactions Inside Your Environment
Since phishing often exploits external notifications and third-party portals, the solution is straightforward: embed secure messaging, forms, and document exchange directly within your authenticated, branded environments—such as your web portal, Salesforce, Microsoft 365, or EHR system.
Here’s what that changes:
- Removes External Notification Risk: No more “view secure message” emails from unfamiliar domains. Instead, alerts appear in-app or within your owned channels, making them much harder to spoof.
- Preserves Trust Signals: Users stay on your domain, with your identity provider, session controls, and familiar UX—reducing the risk of replica pages and deceptive look-alike links.
- Unifies Security and Experience: Fewer detours, lower abandonment rates, and clearer audit trails for compliance. Even Dropbox’s own public guidance warns users about phishing attempts, reinforcing why customer-facing “secure” flows should minimize external links.
This embedded approach aligns with how enterprises are consolidating workflows inside Microsoft 365, Entra ID, and Azure—where authenticated sessions, in-app notifications, and native identity controls reduce phishing risks by design.
The Compliance Multiplier Effect
When secure workflows stay within your authenticated environment, every interaction – whether it’s a message, file, or form – is automatically logged, encrypted, and governed by your existing compliance policies.
That means less ambiguity for auditors, stronger chain-of-custody evidence, and a single source of truth for every communication.
That’s the power of the “compliance multiplier.” It reinforces regulatory alignment while protecting your organization from data leakage, credential harvesting, and unmonitored handoffs – risks often introduced by third-party portals.
What Boards and CISOs Should Ask Right Now
If you’re leading enterprise security or compliance in a regulated environment, these five questions will help reveal hidden phishing risks still lurking in your ecosystem:
- Which workflows still rely on external “secure” portals or links? Inventory any process that sends customers to non-first-party domains, especially for sensitive communications.
- How often are brand-impersonation attempts targeting those flows? Track incidents involving providers like Dropbox, Box, and Zix. Collect examples, timestamps, and outcomes. (Universities and enterprises regularly warn users about Dropbox-themed phishing for a reason.)
- Can we embed instead of redirect? Prioritize high-risk use cases—claims, statements, PHI, loan documents, wealth communications—and bring them inside your identity boundary.
- Are our defenses tuned for “legit-looking” links and social engineering attempts? Modern phishing blends genuine elements with restricted-access files, multi-stage redirects, and AiTM kits. Assume evasion by design. (Microsoft)
- Do we have customer-grade guidance? Public-facing help centers (including Dropbox’s) warn users to beware of suspicious shares. Your brand should reinforce: “We will never ask you to access sensitive messages via third-party links.”
A Practical Migration Path (Six Moves)
Ready to move from awareness to action? Here’s a six-step migration path for CISOs and IT leaders to reduce their phishing risk while improving experience.
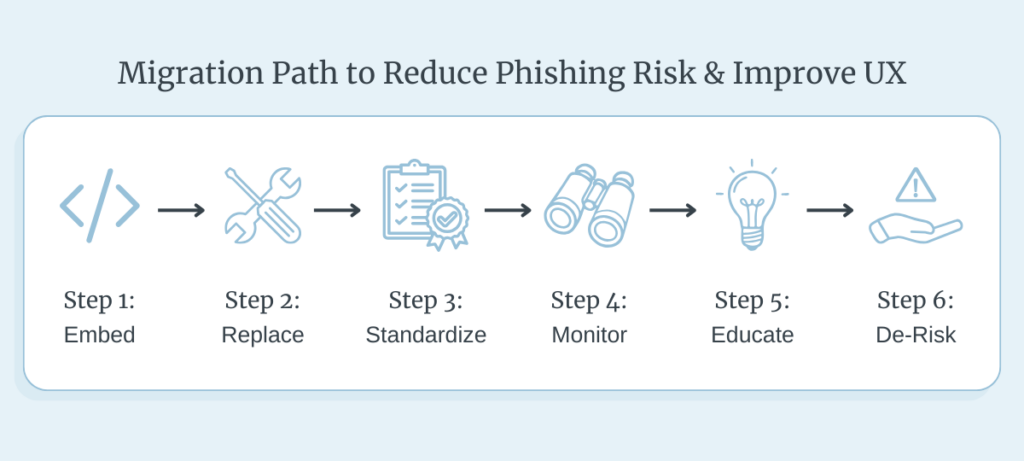
- Embed secure messaging & file exchange in your portal, app, or other core systems (e.g., Salesforce, Microsoft 365) protected by SSO and MFA.
- Replace email links with in-app notifications and short-lived deep links bound to authenticated sessions instead of generic “view message” emails.
- Standardize identity & session controls across all “secure” workflows. Eliminate ad-hoc registrations on external sites.
- Monitor for suspicious activity. Watch for failed logins, unusual referrers, and link trails. Use policy-based throttles to limit exposure.
- Educate external users. Publish a simple “How we contact you securely” page and keep it consistent across channels. When users know the pattern, spoofing stands out.
- De-risk necessary email alerts by using branded, DMARC-aligned communications and avoid generic language attackers can easily clone. Attackers regularly pass basic checks; don’t rely on headers alone.
Bottom Line for Regulated Industries
Financial Services, Healthcare, Insurance, and Public Sector teams can’t afford gray areas in customer trust. The new calculus is simple: external “secure” portals increase phishing exposure and erode user experience, while embedded, first-party workflows reduce both—by design.
That’s the story your board, customers, and regulators will understand – and expect you to act on.
Frequently Asked Questions
How can regulated organizations reduce brand impersonation phishing risks without sacrificing user experience?
Consolidate “secure” communications into your existing portals and apps. Embedding secure messaging, forms, and file exchange within your authenticated sessions (using SSO and MFA) removes ‘spoofable’ notification points and preserves trust signals.
What’s the advantage of platforms with embedded secure messaging versus third-party encrypted email tools?
Embedded secure messaging keeps sensitive interactions within your domain, behind your identity controls, and with unified audit trails—meeting compliance requirements while minimizing exposure to adversary-in-the-middle (AiTM) and credential harvesting attacks.
What’s DataMotion’s role in preventing brand impersonation phishing?
DataMotion provides the infrastructure to bring secure interactions—messages, forms, and file exchanges—inside your own environment. By embedding these workflows into your authenticated systems like Microsoft 365 or Salesforce, organizations reduce reliance on external portals that attackers can impersonate. The result is fewer phishing entry points, clearer audit trails, and a better experience for both users and auditors.
Sources & Further Reading
- The True Cost of Building a Secure Messaging Platform
- The Missing Link in Microsoft Cloud Deployments for Regulated Industries
- The Definitive Guide to Data Exchange: Managing Structured & Unstructured Data
- Microsoft Threat Intelligence: File hosting services misused for identity phishing (SharePoint/OneDrive/Dropbox)
- Darktrace analysis: Legitimate services abused (Dropbox), and AiTM kits using legitimate services
- Abnormal Security: AiTM Dropbox phishing during open enrollment
- KnowBe4 / Armorblox: Zix secure-message impersonation
- FBI IC3 (2024): Phishing/spoofing top complaint category; $16.6B losses (2024)
- Verizon 2025 DBIR: Phishing and pretexting among top social-engineering drivers of breaches
- Dropbox Help Center: Avoid phishing attempts (official guidance)
- UT Health San Antonio: Advisory on Dropbox-themed phishing (practical example)




