The deal is signed; the handshakes are done. But for your legal, HR, and finance teams, the real risk has just begun. Mergers and acquisitions (M&A) don’t just test an organization’s infrastructure; they stress-test its data security to the breaking point.
Between due diligence, cross-company integrations, and countless external exchanges, sensitive data moves faster and farther than ever before.
Each document, message, and form shared across legal, HR, and finance teams carries more than numbers and names — it carries risk. And when those exchanges happen across different domains, email systems, or compliance frameworks, the potential for exposure grows exponentially.
The challenge isn’t just protecting information. It’s protecting it without slowing down the deal.
The Hidden Data Risk Behind Every M&A Deal
Every merger or acquisition involves an all-you-can-eat buffet of sensitive data — financials, employee records, customer information, legal contracts, and board communications. All of it has to flow securely among teams, advisors, and systems that may have never worked together before.
- Financial and due diligence data spanning multiple systems
- Legal communications with external counsel and regulators
- Employee and customer PII subject to GLBA, SOX, PCI, and HIPAA
- Confidential board materials exchanged between new stakeholders
During due diligence, firms must not only assess the financial health of a target — they must also ensure M&A data security and compliance across both organizations. And a single misstep can be catastrophic. Even one unsecured email or outdated sharing method can trigger massive consequences, including compliance violations, reputational damage, or derailed negotiations.
And it’s not hypothetical. The data breach risk during M&A is both real and expensive.
Financial Services Data Protection: Why Stakes Are Higher in M&A
In 2024, the average cost of a data breach hit $4.88 million, up 10% from the previous year (IBM, 2024) — and the financial services sector topped $6 million per breach (American Bankers Association, 2024).
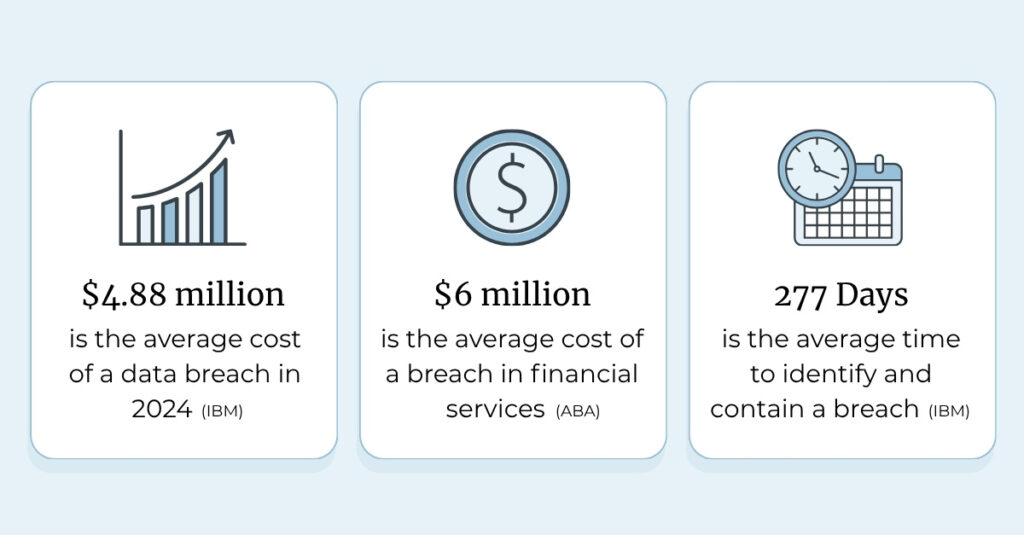
Worse, it now takes an average of 277 days to identify and contain a breach (IBM/Ponemon 2023). During a typical M&A process spanning 6-12 months, a breach could be actively occurring throughout the entire transaction without detection. Imagine discovering that delay after a deal closes — when both parties have already exchanged sensitive data across systems now under one roof.
The lesson is simple: in M&A, data risk doesn’t pause for due diligence.
Why Isn’t Encryption Enough for M&A Data Security?
Most M&A security tools focus on one thing: encrypting the file. But that’s like putting a lock on a package and ignoring how it gets delivered. True M&A data security must protect the entire workflow – the chain of approvals, edits, and handoffs between teams, systems, and organizations.
That’s the missing layer in many due diligence workflows. Data may be secure when sent, but becomes vulnerable when received, annotated, or shared again by another stakeholder. Each handoff introduces risk and slows momentum.
Modern M&A data security demands more than encryption; it requires intelligent workflow security that continuously enforces policy as information moves through each stage of the deal. Without this, organizations face an impossible choice: slow down to manually verify compliance at every step or move fast and hope nothing slips through the cracks.
“You can’t separate deal velocity from data protection anymore. They have to move together.”
Bob Janacek, CEO, DataMotion
That’s the shift defining modern M&A security — a new expectation that protection and performance operate in sync.
So what does that look like in practice?
A Smarter Approach: Embedded, Zero-Trust Secure Exchanges
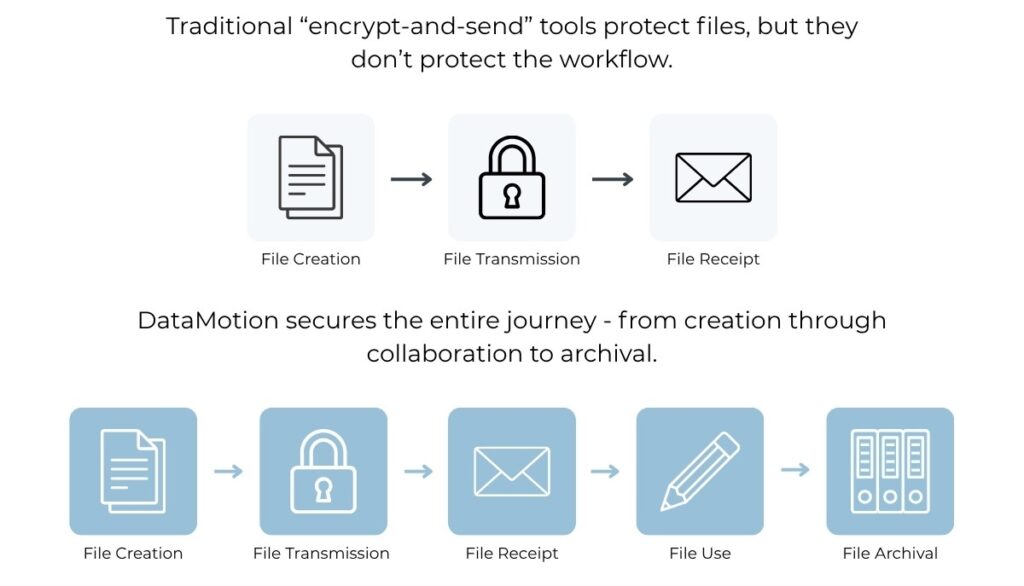
Traditional “encrypt-and-send” tools protect files, but they don’t protect the workflow. Gaps emerge between systems, slowing communication and creating compliance blind spots.
At DataMotion, we believe security shouldn’t slow you down. It should disappear into the flow of work.
Instead of forcing users to step outside their familiar tools, DataMotion embeds secure messaging, document exchange, and workflow automation directly into the systems your teams already use like Microsoft 365, Salesforce, Dynamics, or custom portals.
- No external portals.
- No extra passwords.
- No frustrated stakeholders.
Just secure, compliant exchanges that move as fast as your deal team does.
As a Microsoft partner, DataMotion integrates natively within the Azure and Microsoft 365 ecosystem, giving M&A teams the benefit of zero-trust security, backed by enterprise scalability and MACC alignment.
The integrated approach to secure M&A communications keeps sensitive data within a trusted environment, ensuring compliance without added complexity.
The difference between traditional point solutions and workflow-level security becomes clear when you compare their coverage (see diagram below). Traditional tools secure the moment of transmission. DataMotion secures the entire journey – from creation through collaboration to archival.
Why Embedded Security Delivers
When security lives natively in your workflow, it transforms overhead into operational advantage:
- Policy-Based Routing and Automation: Sensitive data is detected and routed securely, no manual tagging or guesswork.
- Granular Access and Audit Trails: Every exchange is logged, controlled, and revocable — protecting you long after the message is sent.
- Cross-Platform Compatibility: Whether your users are in Outlook, Salesforce, or a client portal, DataMotion keeps communications secure and seamless.
- Workflow-Level Intelligence: AI-assisted tools like the JenAI Suite help teams identify sensitive content and streamline secure interactions, turning compliance into an efficiency multiplier.
Across regulated industries, DataMotion customers regularly report faster communication cycles, fewer manual steps, and stronger compliance outcomes — not by adding tools, but by making security native to their everyday workflows.
Real-World Example: Speed, Security, and Confidence
In complex transactions, secure document exchange and workflow-level automation make the difference between weeks and days.
When two financial institutions merged recently, their combined IT and compliance teams used DataMotion’s Secure Message Center and Smart Secure Forms, embedded in their Microsoft 365 environment, to streamline due-diligence workflows across both organizations.
What once required multiple, separate encryption tools and manual data transfers became a unified, compliant process built into their existing environment.
The result? A 40% faster review cycle, complete audit trails for regulators, and zero friction for external stakeholders — all under a single, zero-trust framework.
That’s the difference between doing secure work and working securely.
➩ See how a 40% faster review cycle could impact your next deal. Explore our solutions for financial services.
Beyond Protection: Turning M&A Communications into Intelligence
The case study above shows how embedded security accelerates deals. But what if your security platform didn’t just protect your last deal? What if it helped you execute the next one faster and smarter?
Most M&A systems are built to protect data, but few are designed to learn from it. Every secure message, form, and exchange represents valuable operational insight: who’s exchanging what, where friction occurs, and how compliance evolves across the deal timeline. But those insights often disappear the moment a deal closes.
JenAI Connect changes that. It automatically captures, structures, and delivers secure communication data (messages, attachments, and form submissions) directly into your Azure environment. Sensitive details are anonymized using AI, ensuring full compliance while unlocking valuable analytics for your team.
With this capability, deal teams can analyze patterns, improve due diligence compliance efficiency, and surface insights that strengthen future transactions – all without exposing confidential content.
That’s the next evolution of secure collaboration for M&A: transforming protected exchanges into communication intelligence that drives smarter, faster, and safer deals.
Security as a Deal Enabler, Not a Detour
Security has long been seen as a necessary brake — a step you take after signing the NDA. But in modern M&A, the firms that embed security early move faster, integrate more smoothly, and inspire more confidence.
Recent data supports that shift. Studies show that companies with stronger cybersecurity postures are more likely to complete deals successfully and maintain higher valuations (ECGI 2023).
Cyber posture has become a key variable in M&A due diligence, influencing both risk assessment and final pricing. In fact, Verizon’s $4.48 billion acquisition of Yahoo became a cautionary tale when undisclosed breaches were revealed post-agreement, ultimately dropping the deal value by $350 million — a reminder that security gaps don’t just expose data; they alter balance sheets.
That awareness has led to a measurable trend: in 2024, there were 226 announced or closed cybersecurity-related M&A deals, up approximately 13.6% year-over-year (Capstone Partners, 2024).
Security is no longer a checkbox, it’s an investment strategy.
Enabling Growth, Not Guardrails
When security lives inside the workflow, it becomes what it should be: an enabler, not a gatekeeper. M&A teams can communicate with confidence, maintain regulatory compliance, and preserve stakeholder trust — all without losing deal momentum.
With DataMotion, protecting sensitive M&A data doesn’t mean adding another system. It means modernizing the one you already have, securing every exchange, message, and document with the same precision that defines your deal strategy.
The Bottom Line
Mergers and acquisitions are built on trust — between companies, leaders, and the data that connects them. Success depends on the ability to share information securely, confidently, and at speed.
With DataMotion, you can do exactly that.
Protect your most sensitive communications. Accelerate your deal velocity. And keep your growth story on track — securely.
→ Book a demo to see how DataMotion helps financial services and enterprise teams safeguard sensitive exchanges during M&A and beyond.
Frequently Asked Questions
During due diligence, how can we share data quickly without increasing our risk?
An embedded Zero-Trust approach eliminates the trade-off between speed and security. By integrating secure document exchange and automated compliance into the tools your team already uses, you remove friction and manual delays while ensuring every exchange is verified and protected.
How does workflow automation enhance secure M&A communications?
Automation ensures that every document and message is routed securely, logged, and compliant—reducing manual effort while maintaining speed and accuracy.
We already use enterprise platforms like Microsoft 365 and Salesforce. Why do we need another tool for M&A?
DataMotion isn’t another tool; it’s a security layer that enhances the platforms you already use. It embeds zero-trust workflow automation directly into systems like Microsoft 365, Dynamics, and Salesforce, enabling secure collaboration without forcing users to switch contexts or slow down.
Does DataMotion support M&A due diligence compliance standards?
Yes. The platform is HITRUST CSF® Certified and supports compliance with FINRA, SOX, PCI DSS, HIPAA, and more—ideal for financial services and regulated industries.
Can DataMotion integrate with existing Microsoft workflows?
Absolutely. DataMotion is built on Microsoft Azure and integrates seamlessly with Microsoft 365, Dynamics, and Entra ID, ensuring secure collaboration within your existing ecosystem. As a Microsoft partner with MACC alignment, DataMotion is available through the Azure Marketplace, making procurement and deployment streamlined for enterprise teams.