Why Teams Start Building Secure Messaging in the First Place
Most organizations don’t set out to build a secure messaging platform.
They get there because something isn’t working.
Messages technically get delivered. Compliance boxes get checked. But the experience feels harder than it should. Customers struggle to respond. Portals don’t sync. Workflows feel fragmented. Friction becomes “just how it is.”
So teams patch. They customize. They extend what they already have.
And when the experience still doesn’t improve, the instinct becomes: maybe we need to build.
That decision rarely starts as an engineering ambition. It starts as an attempt to fix a customer experience problem that has quietly become normalized.
When regulated organizations struggle with secure messaging, the conversation often eventually turns to whether they should build something themselves or rely on an external platform. That framing is understandable, but it rarely captures the full scope of what’s actually at stake. For enterprises under strict regulation, the deeper question becomes: who owns auditability, workflow integrity, scalability, and the ongoing evolution of the experience over time—and who bears the consequences when those elements break down?
Below, I walk through the less obvious technical, operational, and compliance burdens that emerge when organizations try to build an enterprise-grade secure messaging capability.
Along the way, it becomes clear why experience problems persist when secure interactions are treated as isolated features rather than connected parts of a broader workflow.
The Regulatory Iceberg
Imagine an iceberg floating in the water. Above the waterline, you see the visible features of a secure messaging solution, the parts that are easy to compare in a vendor demo or an internal prototype. Beneath the waterline lies the hidden complexity, the parts that require constant engineering, governance, and compliance work over the life of the system.
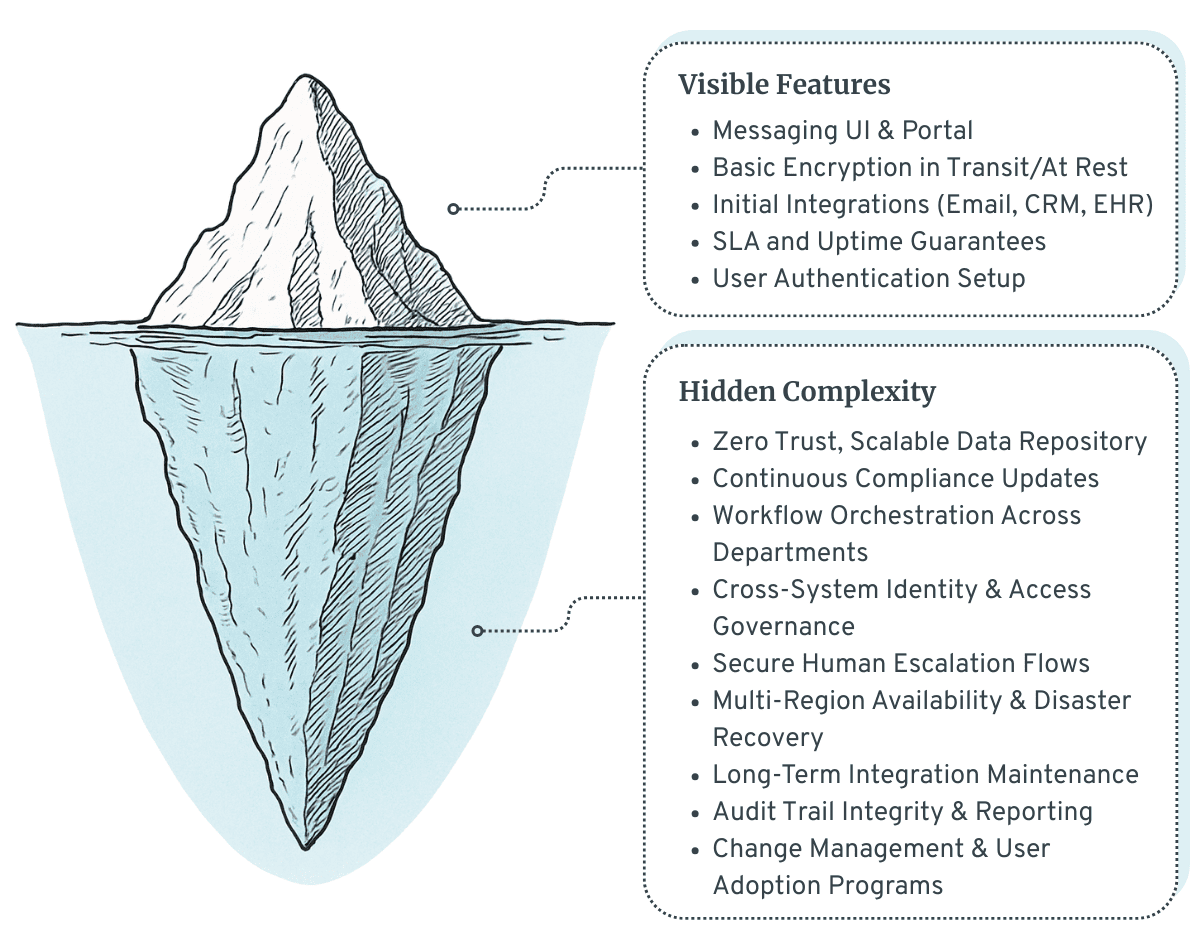
The Visible Part of the Choice (What You Normally Compare)
On the surface, the choice looks simple:
- Build (in-house or outsourced): Control, customization, potential cost savings for very limited scope.
- Buy (commercial vendor / unified platform): Faster time-to-value, vendor maintenance, predictable SLAs.
Those are necessary considerations, but insufficient for regulated enterprises. The real risks hide beneath the surface: regulatory upkeep, workflow complexity, cross-system integration, user adoption, governance structures, and the operational realities of keeping the system secure and audit-ready for years.
The Deep Technical and Operational Complexity of Building an Enterprise-Grade Secure Messaging Platform
If your team is seriously considering building, expect to design and then maintain the following, each of which is non-trivial and costly:
1. End-to-End Auditability and Compliance Plumbing: You must capture immutable, tamper-evident logs; integrate with security monitoring tools; produce audit trails that survive legal holds and regulatory scrutiny; and enforce granular retention and access rules. Designing and validating these pipelines is far more complex than simply enabling logging.
2. Workflow Orchestration Across Channels: Modern secure messaging isn’t just email. It spans structured forms, large attachments, case updates, portal integrations and status tracking, often flowing across departments and systems. Each step must preserve security context, maintain user identity integrity, and enforce business rules without introducing bottlenecks or compliance gaps. And it must be easy to use.
3. Integration with Enterprise Systems: CRMs, EHRs, identity providers, document repositories, and case management tools all need to plug in securely. Each integration carries authentication, authorization, data exchange, and version management requirements that must be maintained through vendor updates, regulatory changes, and infrastructure upgrades.
4. Scalability, Availability, and Resilience: Your architecture needs to handle spikes in demand, regional load balancing, disaster recovery, and cyber incident response, all without breaking the trust model. Achieving these demands thoughtful design, testing under failure conditions, and ongoing capacity planning.
5. Secure Human Escalation Workflows: Many organizations need automated intake (AI chatbots, self-service portals) with escalation and response from an online agent or out-of-band back-office expert, while preserving security, chain-of-custody, and audit metadata. This requires seamless bi-directional integration between systems.
6. Continuous Compliance Burden: Regulations shift. Security baselines evolve. Staff turnover happens. A homegrown system needs ongoing testing, governance reviews, and updates to remain in line with industry standards, certifications, and audit expectations — year after year. And you carry the entire cost, in budget, staff hours, and opportunity cost.
In short: every “simple” feature has layers of governance, integration, and monitoring requirements that multiply quickly.
Why Experience Problems Persist—Even After You Build
What’s often overlooked in build-versus-buy discussions is that secure messaging is rarely the root problem organizations are trying to solve.
The real issue is experience fragmentation.
Messages arrive in one place. Forms live in another. Portals don’t always reflect the same state. Customers move between systems that weren’t designed to work together, and internal teams spend time compensating for gaps the technology never closed.
Building a secure messaging capability may address one part of that equation—but it doesn’t automatically fix how information flows, how users interact, or how the experience feels end to end.
That’s why many organizations invest significant time and resources into building secure messaging, only to find that customer friction remains. The security problem may be solved, but the experience problem persists—because it lives across workflows, not inside a single tool.
Why Some Organizations Prefer a Unified, Vendor-Maintained Platform (Beyond “It’s Faster”)
If you accept that the difficult parts above are real, a modern unified platform provides a different risk profile:
- Centralized Compliance Posture: Vendors that certify against frameworks (HITRUST CSF®, SOC2, HIPAA mapping, FINRA) maintain much of the evidence and control baselines you’d otherwise have to produce and update in-house.
- Integrated Primitives Across Capabilities: Messaging, secure forms, document exchange, self-service chat, and live escalation all share common authentication, logging, and retention logic, which reduces integration work and eliminates brittle bridges between point solutions. Taking a unified approach to these greatly reduces end-user complexity and friction.
- Operational Services You’d Otherwise Staff For: Capacity management, disaster recovery readiness, uptime SLAs, and security patch pipelines are handled as part of the service rather than your internal operations.
- Feature Evolution Without Re-Platforming: As needs grow (simple messaging → interactive forms → complex case management → secure escalation), a platform with enterprise depth avoids fragmented workflows, costly rebuilds and repeated procurement cycles.
A unified platform isn’t simply a convenience; it’s a way to consolidate complexity and reduce the operational surface area your organization must directly manage. Of course, there are cases where building is the right move, but only if you’re ready to treat it like a product with a lifecycle, not a one-off IT project.
When Building Still Makes Sense — And What It Must Cover
Building is justifiable when you truly require capabilities no vendor supports, or when you have long-term, large-scale requirements tied to unique business processes. If you choose this path, you must treat it as a product with a lifecycle, not a project with an end date.
This means planning for:
- Compliance-By-Design: Audit trails, role-based access control, immutable storage, and evidence generation for regulators.
- Cross-System Orchestration: Ensuring every integration point maintains consistent security and governance models.
- Workflow Adaptability: Allowing secure messaging to evolve into case intake, approvals, escalations, and analytics without requiring re-architecture.
- Operational Resilience: Establishing runbooks, incident response plans, disaster recovery playbooks, and governance committees to oversee the system.
Practical Decision Checklist for Choosing a Secure Messaging Platform in Regulated Enterprises
1. Map Regulatory Requirements: Retention, eDiscovery, audit scope, and specific certifications needed.
2. Inventory Integration Points: List every system that will connect to the secure messaging platform today and in the organization’s roadmap, and evaluate the integration and maintenance effort for each.
3. Estimate Ongoing Ops Cost: Include monitoring, testing, governance meetings, security updates, and documentation.
4. Plan for Human Escalation: Ensure security, privacy, and audit trails persist through automated-to-human handoffs.
5. Run a Proof of Concept: Validate audit log portability, integration behavior, and escalation flows before committing to a path.

➡︎ Download a ready-to-use version of the Secure Messaging Buy vs Build Checklist to share with your team.
Bottom Line
For regulated organizations, “buy vs build” is ultimately a question of who carries the long-term governance, compliance, and operational complexity. Building your own secure messaging stack can seem appealing at first — until the layers of audit support, workflow orchestration, integration upkeep, and compliance evolution start consuming more resources than expected.
If your mission is to direct engineering and operational focus toward core business priorities rather than running a perpetual compliance and workflow integration program, a unified vendor platform, one that already includes messaging, forms, document exchange, chat, and secure escalation, can materially reduce risk, effort, and long-term cost.
Explore how DataMotion’s unified, Microsoft-native platform can help you stay ahead of compliance demands, streamline integrations, and accelerate ROI, without the hidden costs of building from scratch.

FAQs: Buy vs Build Secure Messaging in Regulated Industries
Why is “buy vs build” a bigger decision in regulated industries?
In regulated sectors like healthcare, finance, and government, secure messaging platforms must meet strict compliance, audit, and security requirements. Choosing to build means you’ll own all ongoing governance, integration maintenance, and risk management. Buying shifts much of that responsibility to a vendor with established certifications and operational processes.
What hidden costs should I expect if I build a secure messaging platform in-house?
Expect recurring costs for compliance updates, system integrations, disaster recovery planning, incident response, and security patching. These aren’t one-time expenses, they grow over time as regulations change, infrastructure evolves, and new integrations are added.
How does a unified secure messaging platform lower compliance and operational risk?
A unified platform handles messaging, forms, document exchange, and chat under the same authentication, logging, and retention rules. This avoids fragile point-to-point integrations and lets the vendor maintain compliance certifications like HITRUST CSF®, SOC 2, HIPAA mapping, and FINRA, reducing the workload for your internal teams.
When is building a secure messaging platform the right choice?
Building makes sense if you need capabilities no vendor offers, have in-house engineers with deep compliance expertise, and are ready to treat it as an ongoing product. That means budgeting for governance, security updates, feature upgrades, and compliance changes for the life of the system.
What are the advantages of a Microsoft-native secure messaging platform?
A Microsoft-native platform integrates directly with Microsoft 365, Azure Active Directory, and other Azure services, using your existing identity and compliance framework. This can speed up deployment, improve adoption, and qualify for Microsoft Azure Consumption Commitment (MACC) benefits, which can accelerate ROI.




