Healthcare IT: Challenges and Opportunities in Secure Exchange
DataMotion Director of Product Andrew McKenna sat down with Content Manager Andrea Meyer and Digital Marketing Specialist Sarah Parks to chat about his experience at the recent HIMSS22 conference, which took place in Orlando, Florida. As a newer addition to Team DataMotion and a first-time HIMSS attendee, Andrew offered unique perspective, sharing highlights of conversations with fellow attendees, observations on the current state of the healthcare IT landscape, and thoughts on where he sees the future of digital exchange within healthcare.
DataMotion: Andrew, thanks for speaking with us today. Before diving into HIMSS, your learnings, and discussions around secure exchange, we’d like to learn about you. Tell us a bit about your role and background.
Andrew McKenna: I have a degree in Computer Science from Mount St. Mary’s University, and recently joined DataMotion as our Director of Product. My role links our engineering, operations, customer success, and sales teams together. I am responsible for the full spectrum of product management, from product strategy to road mapping, culminating in the delivery of products to the market. I love this role because I have the opportunity to see use cases in action, how stakeholders leverage our products, and how we can improve. It’s exciting to discuss and plan the future use cases of our products!
Prior to joining DataMotion, I spent most of my career in product and engineering roles in financial services. I also spent time in the supply chain software space. Throughout my career, I have linked disparate systems to create frictionless digital workflows, allowing data to quickly travel from point A to point B for efficient processing. These workflows helped level silos that were created during previous paradigms of technical revolution. My approach has historically been doing all of the above while striving for end user delight, whether it be a factory user in a supply chain, a financial advisor, or a banking operations user.
DM: This was your first time attending the HIMSS conference. As a first-time attendee, what was the experience like?
AM: As I roamed the Orlando Convention center floor, the first thought I had was wow, this is HUGE. I thought I had been to large conferences before, but the size of the exhibitors’ hall was truly overwhelming. HIMSS was my first conference since the COVID-19 pandemic, and my first healthcare conference ever. I was ready to learn about old and new problems the healthcare industry is facing. Because these problems are new to me (from a healthcare perspective) I was excited at the prospect of thinking through innovative solutions to very different and difficult use cases.
While walking the floor, I met with API and call center companies, EMR (Electronic Medical Records) and EHR (Electronic Health Records) vendors, system integrators, emerging technology providers, healthcare payors and providers, and many others. It was great to finally connect in-person with current and potential partners! I was fortunate to walk the halls with our CEO, Bob Janacek. In doing so, I met quite a few industry leaders who are familiar with DataMotion’s history and vision. While speaking with these folks and hearing their stories, I had an opportunity to discuss potential workflows and use cases for our products. Despite the different industry verticals and varying pain points, we were all there with the goal to improve healthcare technology and the flow of information. This commonality made for a wonderful introduction to the needs across other technology companies and the industry as a whole!
DM: You recently joined Team DataMotion, so for context, you attended a new event, in a new role, exploring a new industry. Tell us how DataMotion’s products, services, and mission shaped your perspective going in.
AM: To level set my learnings, it is important to first define who we are at DataMotion. In short, DataMotion is a secure communications platform. At its core, our platform consists of a governed, trust no one, trust nothing database. Let’s focus on security for a moment–the security level of our platform means that every single communication that is transmitted via DataMotion is transmitted securely and compliantly. In fact, our platform is so highly secure that even DataMotion’s admins cannot see any transmitted data!
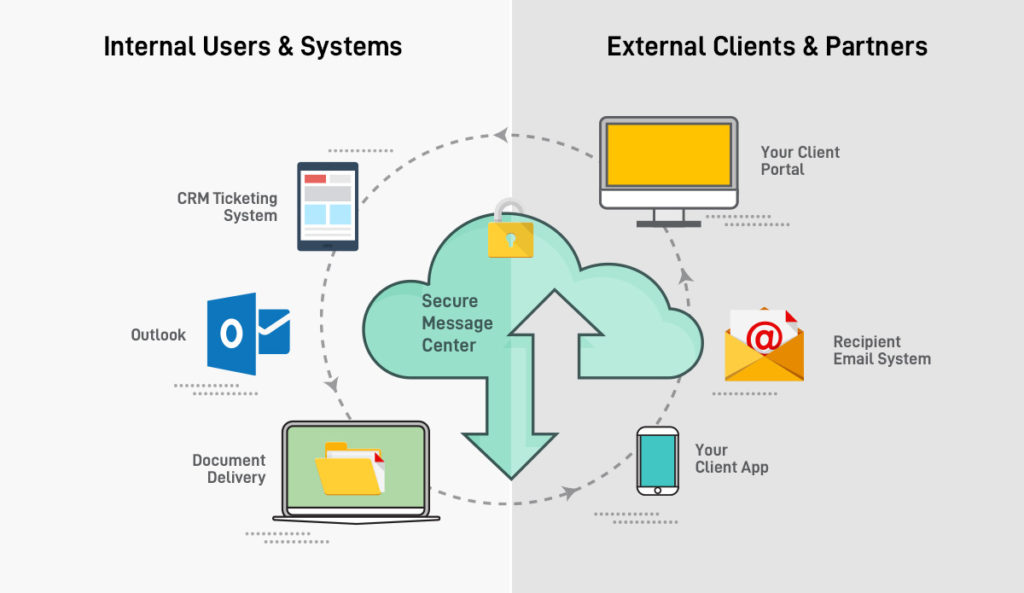
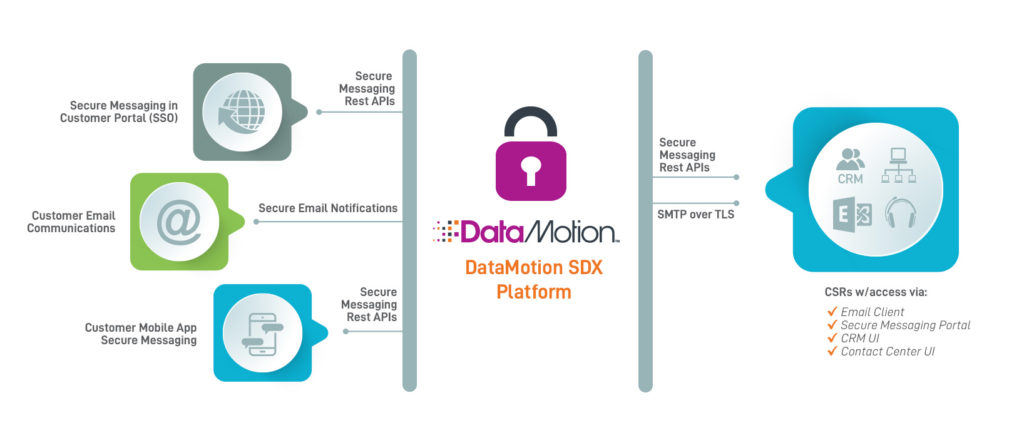
The other key of our platform is how we deliver to our customers. We provide well-designed RESTful APIs and other flexible connectors that customers can stitch into their systems. This enables seamless integrations for secure data transmission, including transmissions between disparate systems. The final key to highlight is the fact that we have applications and key integrations available. As a Communication Platform as a Service (CPaaS) organization, we meet our customers where we are needed in the method that is required to provide a simple, right-sized solution for secure transmission of content. We have a long history that has brought us to where we are today. This history has shaped our vision for the future, and I am excited to be a driver of that vision.
DM: Can you tell us a little bit about DataMotion’s contributions to secure exchange in the healthcare ecosystem?
AM: As a technology company that began in the regulated space, healthcare is a natural extension for us. We enable the secure, compliant communication that protects our customers and their patients’ health information. Since 2012, DataMotion has been a member of DirectTrust™, providing a safe, secure, and compliant way to transmit health records between providers, allowing the fast, efficient connection of patient information to the correct part of the healthcare ecosystem.
Payors, providers, patients, and others in the healthcare ecosystem need to be securely linked, with content flowing across verticals. DataMotion is an active player in this area—serving as the nation’s catcher’s mitt for COVID-19 test reporting to the government is one example. Another example is how we have enabled secure communications for a state agency that facilitates ambulatory care for patients. DataMotion also provides solutions for health insurance companies that simplify secure communications processes for both customer service agents and policyholders alike.
DM: This was an enormous event, with attendees from just about every aspect of the healthcare ecosystem, each with their own unique challenges and goals. You had a lot of one-to-one discussions—tell us about your conversations in general and any recurring themes.
AM: Many of the conversations centered on secure data transmission being critical in the world of healthcare. I discussed different solutions with representatives from call center organizations, whose focus is on the industry of home health app providers. If Direct is not available, fax and other early-form CPaaS services still seem to rule for many. As such, most of the folks I spoke to did not have a solution for transmitting content securely and compliantly outside of the specific customer’s four walls. Yes, they can collect the pertinent data and they can send the data within their network. But actually crossing into another provider’s ecosystem seems to be an afterthought.
DM: Based on these conversations, what are your thoughts on the current state of healthcare IT?
AM: I found myself speaking within my comfort zone for much of the show, coming across software providers and integrators that are well known in the financial services vertical. Our conversations led back to the challenges facing healthcare IT.
Today, there are regional applications that handle local to local transfer of pertinent data. But not all regional applications play well with others. For example, some don’t accept specific transmissions, causing failover to manual processes. This brought back memories of transferring my children from one primary pediatrician to another. We had requested electronic records transmission; it was sent. The new pediatrician received the records; however, their EHR could not translate the attachment. Therefore, the records were faxed before our first appointment and we brought a printed record.
Let that sink in: in 2022, because the systems didn’t get along, a nurse at the new office had to manually enter the entire medical history of our children – from a fax!
This problem statement resonates across industries. Like financial services, healthcare is an area where protection of content would be an issue if a solution like DataMotion was not present. These organizations require a service like ours. Without DataMotion, our customers have to build their workflows in addition to building secure messaging protocols. The reality is that DataMotion does the heavy lifting of providing a secure, governed, compliant solution that can be inserted where required.
DM: You mentioned having discussions with representatives from other API companies during the conference. What are some of the larger themes that emerged from those conversations?
AM: Many API companies talked about potential synergies with DataMotion and how, together, we can connect the entire world of payers, providers and patients efficiently and securely. Sure, there are a variety of APIs available for a whole world of needs. But how can you be sure those APIs are secure and will fit in an organization’s workflow? These elements of secure connection and of trust were the commonly-mentioned gaps that came up across many of the conversations. One aspect of these discussions that resonated with our fellow API companies was DataMotion’s customer self-service portal (CSSP), which fills these gaps in the market.
DM: Tell us more about these companies and their approach, DataMotion’s solutions and customer self-service portal, and how it helps the market.
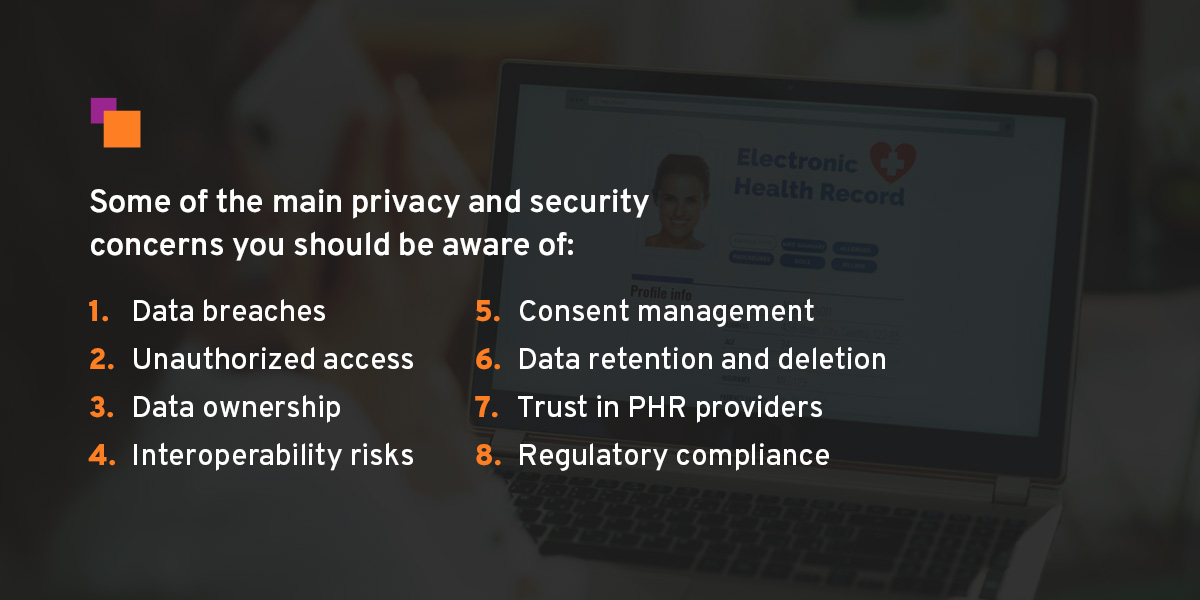
AM: The API companies I spoke with handle their areas of expertise well. But there is much more work to do concerning the secure transmission of data. When it comes to protecting personal health information (PHI) and remaining HIPPA compliant while data is transmitted (and while it is at rest), there seems to be a major gap in the market. There are many mature API companies that offer different options. When speaking with them, their default answer is, yes, our code is solid, go build your solution.
DM: Let’s follow up on this—could you chat for a moment about DataMotion’s approach and how we fill some of these market gaps?
AM: Yes! DataMotion provides mature APIs that developers use as a foundation for their development process. In addition to providing military-grade encryption, DataMotion allows customers to try before they buy by testing our APIs in a secure environment. With our portal, users can see our APIs in action as part of their secure exchange workflow. We offer complete modern data exchange, balancing secure, compliant communication with superior usability by leveraging our APIs, connectors, and prebuilt solutions.
DM: You also mentioned that you spoke with attendees representing call center IT departments. Tell us a bit about those conversations, and how DataMotion helps call centers expand their services?
AM: When talking to attendees from call center software companies, it was clear there is a tremendous need for the simple, frictionless, efficient, and secure transmission of content, while maintaining compliance and a high level of customer service.
DataMotion provides the ability for call center teams to expand their services to include the secure and compliant transmission of PHI and personally identifiable information (PII) as well as other sensitive data. And they can do this while maintaining their natural workflows. Secure and compliant communication is a cornerstone of their daily operations. Key to these conversations is that DataMotion can link them, through Direct Secure Messaging, to EHR applications.
DM: You mentioned that you talked to software providers who are attempting to digitize healthcare. What resounded with these folks, and what topics came up?
AM: Yes, these were some fascinating conversations. These organizations are working toward digitization of the healthcare ecosystem and they need to play well in the sandbox of modern systems. In some cases, legacy communications are used as an important failover for more modern methods. While this is a workable back-up, in many of these cases the end user is leaving their workflow or system to achieve what I like to call a break-glass procedure—in case of emergency, break glass and grab the fire hose. While this is functional, it is not optimal.
DataMotion’s secure content exchange solutions keep our clients and their customers in an ecosystem that is familiar to them while staying compliant. Because of this frictionless process, there is no need for users to create another username and password, or to enter a foreign portal. There are no extra steps to get content to the provider that needs health records, or the results of a home health application or device. And thanks to DataMotion’s APIs, there is no need to bring a device back to an office to securely and compliantly download data. Legacy CPaaS methods are still important, and will be for years to come. But how can they be delivered with simplicity in mind? That is one of the goals of DataMotion’s vision and strategy.
DM: Let’s look into your crystal ball. Based on your conversations and the overall themes at HIMSS, what do you see is the future for healthcare IT?
AM: Absolutely! I would be remiss if I didn’t include future views and workflows that were prevalent in conversations at HIMSS. There are “new” protocols coming to light; many of these have been in existence for quite some time, but with limited adoption. There are also new use cases coming onto the scene, as there’s an enormous push to gather any and all information about a specific patient’s care.
In addition, there are new technologies that provide endpoints to retrieve data from existing platforms. However, there is a resounding hesitation that I need to acknowledge. These newer technologies need to be weighed and vetted. It is critical that the content (a.k.a. the payload) is protected at every step. From a vision perspective, these elements are the cornerstone of our secure exchange solutions.
DM: It sounds like your first HIMSS conference was an eye-opener for you, and you learned a lot about the industry landscape and its pain points. Would you like to share any closing thoughts?
AM: The American healthcare ecosystem is begging to be optimized and digitized. There is technology in place to protect the patients, providers, and the payers; however, the industry needs to take a step back to assess the want to digitize. When they take that step back, they will find that a core segment of solutions are available to them that facilitate the secure transfer of the most sensitive data in the world.
DM: Andrew, thanks for taking the time to sit with us and share your takeaways.
AM: It’s my pleasure—I’m already looking forward to next year’s conference!
We invite you to learn more about DataMotion, our healthcare-focused solutions, and how we can keep your organization’s data secure and compliant. Visit our website or contact our team of security experts for a quick demo.