Your “Secure” Email System Is a Phishing Gateway
These systems are dangerous — and your organization can’t afford the risk.
Keep users protected and engaged inside your trusted environment — not external portals.

You Secured Everything… Until You Didn’t
You’ve hardened your customer portal with multi-factor authentication and zero-trust architecture.
Your security team spent years protecting every entry point.
Then Comes the Weak Link
A customer needs to share sensitive documents — and you redirect them to Zix, Box, or another standalone “secure message” platform.
You just trained them to click links to external portals and enter credentials on unfamiliar domains.

The Hidden Cost
- Phishing is just the start. Every external “secure” portal — no matter how compliant — creates blind spots in your control, compliance, and customer experience.
- Attackers know this. They impersonate secure message notifications because your customers have been conditioned to expect them.
- Each redirect adds risk. What feels like user friction is actually an attack surface you created.
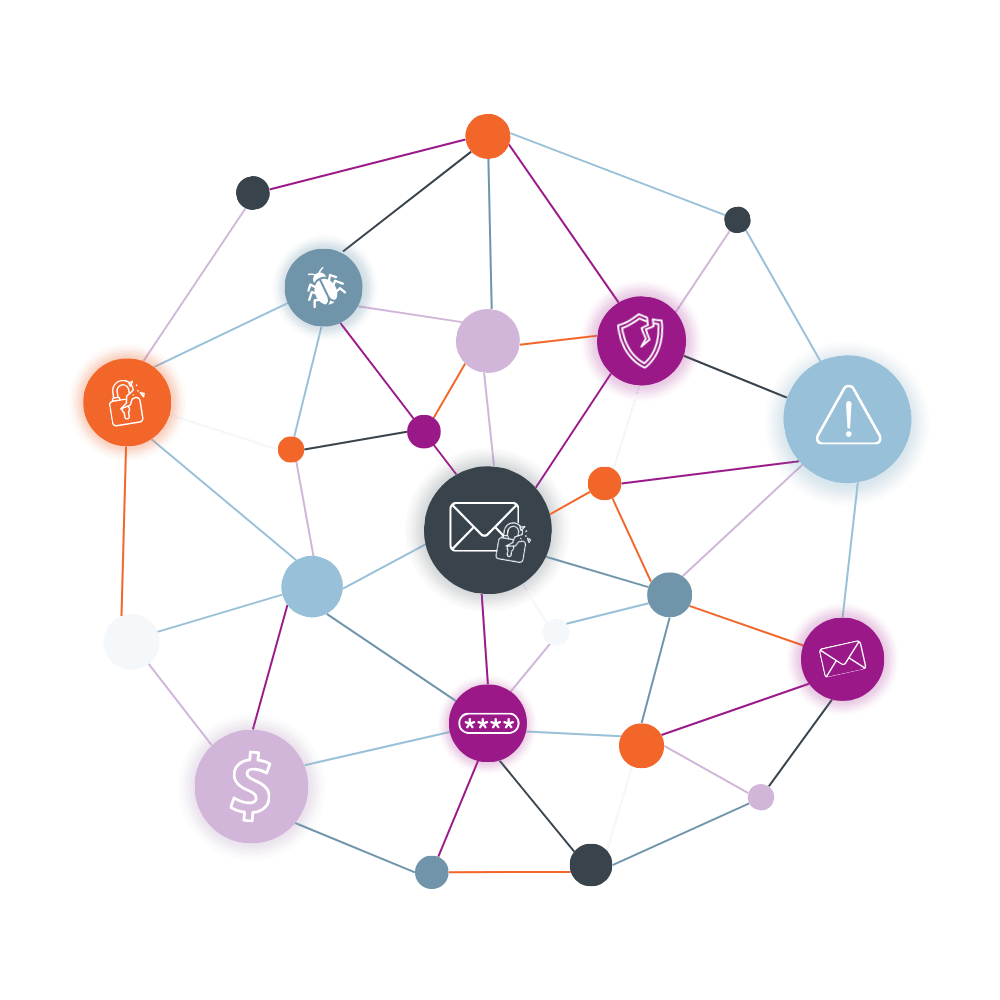
The Problem: "Secure" as a Separate Destination
The risk isn’t just phishing—it’s any point where data, users, or authentication steps move outside your trusted environment.The Old Model Creates Risk
- Customer receives: “You have a secure message”
- Customer clicks link to external domain
- Customer creates new credentials on platform they can’t validate
- Customer enters sensitive data outside your security perimeter
What Attackers Exploit
- Users trained to click “secure message” notifications
- Unfamiliar domains customers can’t verify as legitimate
- Login pages easy to spoof
- Credential harvesting disguised as security

What Your Security Team Faces
- Data flowing through systems outside your control
- Audit trails scattered across vendors
- Compliance monitoring spanning disconnected platforms
- Incident response requiring third-party coordination
The Solution: DataMotion Secure Message Center
Eliminate the attack surface. Keep communications inside your security perimeter. By keeping messages, forms, and files inside your digital ecosystem, you eliminate the weak link between security and experience that standalone platforms introduce. The DataMotion Secure Message Center embeds directly into your existing portals as a unified communications platform—so secure exchanges never leave your trusted domain and identity infrastructure.
No External Portals
Communications happen inside your domain with your SSO. Customers authenticate using credentials they already trust.
Centralized Security Control
Zero Trust architecture, HITRUST CSF® Certified infrastructure, and unified audit trails inside systems you control.

Integration, Not Replacement
Works with Microsoft 365, Salesforce, Genesys, Google Workspace, and your custom portals. Native SSO with major providers.

Proven Enterprise Implementation
Structured onboarding that de-risks complexity. We work with your teams and system integrators from kickoff to steady state.
Deploy the Right Way: No-Code, Low-Code, or Pro-Code
No External Portals
Fully branded secure messaging portal configured to your requirements. Our team handles setup while you focus on change management.
Best for: Organizations needing rapid compliance without custom development.
Widget Integration
Pre-built widget embeds into your portals and mobile apps. Customize branding while our API handles encryption infrastructure.
Best for: Quick deployment with brand customization.
REST APIs
Complete control with comprehensive APIs for messaging, provisioning, and administration. Build your exact vision.
Best for: Full customization of user experience.
Real Impact Across Regulated Industries
Financial Services
Meet FINRA/SEC compliance while eliminating credential phishing vectors. Client communications that strengthen your security posture.
Healthcare
HIPAA-compliant patient messaging that embeds directly into your patient portal – eliminating the need for patients to navigate to separate, unfamiliar secure message domains.
Public Sector
FedRAMP-authorized secure communications on infrastructure you control. Stop training citizens to click suspicious links.
The Proof Is In The Numbers
-
2 KActive organizations
-
10 MActive users
-
32 %Support reduction
-
48 %Efficiency gain
Beyond Phishing:</br>The Hidden Risk of External Trust Models
Every time your customers interact with a standalone secure platform, you lose visibility, audit control, and brand trust. DataMotion keeps every exchange within your perimeter—so you control not just the security, but the experience.
Every redirect to standalone “secure message” platforms conditions customers to click suspicious links, enter credentials on unfamiliar domains, and trust external portals they can’t validate.
This isn’t security. It’s an attack surface with a compliance certificate.
See how we eliminate external phishing vectors while integrating with your existing infrastructure.
Schedule a Security Consultation
"*" indicates required fields






